New *Notion users and businesses often have privacy and security concerns with Notion such as:
- “is Notion secure?”
- “is it okay to store passwords in Notion?”
Here are two such examples from our community:
Wondering if it is smart/secure enough to share passwords with [my VA] through Notion? The page would be private to me and her.
I am not seeing anywhere something about how to archive personal documents like Children School Reports or even digital copies of Passport and other important documents.
These are definitely questions that many *Notion users have both before and after adopting Notion. This article will review the current state of security and privacy in Notion so you can make decisions that are best for yourself and your businesses. Notion is great for a lot of things, but depending on your use cases and needs for privacy, it may not be right for you.
Note: I am not a security expert, but I know enough about securing web applications and GDPR-style privacy concerns to help you understand the basic concerns. Please consult with a security expert before making any decisions about your or your customers’ data.
Security Concerns
TL;DR
My current understanding of Notion’s security:
- ✅ Encrypted at rest
- Meaning that Notion’s databases on their side are encrypted.
- ✅ Encrypted in transit
- Meaning that traffic to/from Notion’s servers is encrypted.
- ✅ SOC2 Compliant
- SOC2 compliance is a rigorous security audit process that checks that companies are following good data hygiene and internal security processes. It’s both difficult to attain and expensive as hell to do so.
- ❌ End-2-End Encrypted (”E2EE”)
- The encryption/decryption of your data is maintained by Notion Labs, not you.
Can/should I store passwords in Notion?
In short: Absolutely not.
You should use a password manager. Examples of two options for storing and sharing your passwords are:
Here is a previous direct quote from a Notion employee that I have been given permission to share (emphasis mine):
Notion as a platform is not designed for holding information such as legal docs, passwords, bank statements – while we take security seriously and are continuing to 1) bolster security/privacy features and 2) build our legal/compliance team and become SOC2 certified [editor’s note: they achieved this since this quote was given], many platforms are designed specifically for the purpose of securing sensitive information. Would recommend using those for any of the aforementioned types of content!
Both 1Password and LastPass have the concept of “shared vaults” which allow you to share authentication details with your employees and collaborators. Please use a password manager!
Is Notion Secure?
Let’s see what Notion says on their Security page:
We use TLS 1.2 to encrypt network traffic between users’ browsers and the Notion platform. We also use AES-256 bit encryption to secure your database connection credentials and data stored at rest.
Notion’s traffic to-and-from its servers is encrypted, so the traffic between your devices and Notion’s databases is encrypted, meaning if someone were to view that traffic, they would not be able to see/understand your data.
Notion also encrypts your data “at rest”. Microsoft has a great description of what this means:
Encryption at rest is designed to prevent the attacker from accessing the unencrypted data by ensuring the data is encrypted when on disk. If an attacker obtains a hard drive with encrypted data but not the encryption keys, the attacker must defeat the encryption to read the data.
Fantastic, that’s what we want, and what Notion offers.
Now, Notion is not “end-to-end encrypted” (”E2EE”). Since Notion maintains the necessary keys to encrypt and decrypt your data, you are not in charge of the encryption/decryption process. In general, this means you should never use it to store passwords, bank accounts, credit cards, health data, etc. Again, your password manager is a much better place for this kind of data.
Another interesting by-product of this is that, via Notion’s support system, you can be requested to give access to your documents to provide support. This essentially means that any Notion employee can see anything in your space. If your data were end-to-end encrypted, this generally would not be possible without the necessary information to decrypt your data.
As a counter-example to this, when I set up my vault in Obsidian, I created a private key/password that is used to encrypt/decrypt my data. Now even if my data was compromised, in order for a malicious actor to see my data, they‘d have to also have my private key. One of the trade-offs of this? If I lose my private key or forget my password, I could lose access to my data. Yikes!
Now, personally I think that if you are concerned with end-to-end encryption, I’d expect you to have one of the two things enabled on your computers:
After asking the folks who’ve been aggressively campaigning for end-to-end encryption, the majority of them don’t even have similar features enabled on their machines. Go figure. 🙄
So…why u no E2EE, Notion?
E2EE would likely be incredibly difficult to do in a collaborative environment. Collaborating would likely be slower, and I’m not sure how it’d even work with real-time editing (holy complex!).
Which is why we see apps like Obsidian and Standard Notes that are “single-player” only. You may want to consider something like those apps if you are primarily looking to organize your personal documents. I’m a huge Obsidian fan and use it daily for thoughts and notes. I use Notion typically for collaborating and higher-order strategic work, and Obsidian is what I consider more my “second brain” layer. Maybe Notion is my third brain? 🤓
Multi-factor Authentication
Editor’s note: At the time of the initial writing of this article (March, 2022), Notion did not support multi-factor authentication out-of-the-box. As of April of 2023, Notion has first-party support for multi-factor authentication. I have updated this section to reflect that.
Many services offer an additional security step which gives you a prompt on a secondary device during sign-in so if your password is compromised, your account will still be safe. Notion offers a “magic link” sign-in which allows users to log in via an email without a password. This means if a user’s email is compromised, their Notion account may be as well.
So it’s highly recommended you enable 2-step verification on your Notion account. You will first need to set a password and then you can use a software or hardware solution to generate your one-time password on sign-in.
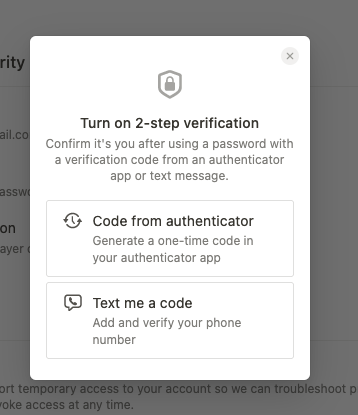
You have two options for verification: (1) a code texted to your phone number or (2) using an authentication device such as Google Authenticator, Authy, et al. I highly recommend using #2 or even a hardware-based solution as #1 tends to be less secure.
Notion does offer single-sign-on via SAML on their enterprise plans, but this means more cost to you and your business and/or a third-party sign-on provider to enable secure accounts. This might not be a big deal to a larger company that already has such systems in place, but be aware that it is a limitation of anything less than Notion’s Enterprise plan.
Privacy Concerns
Importantly, it’s not possible to hide the emails and names of the Members and Guests you invite into a workspace. So while it’s possible to control who gets into your Workspace, any member or guest can see emails of any other member or guest that’s been invited into your workspace. You simply have to open the “Settings & Members” settings in Notion to see the emails.
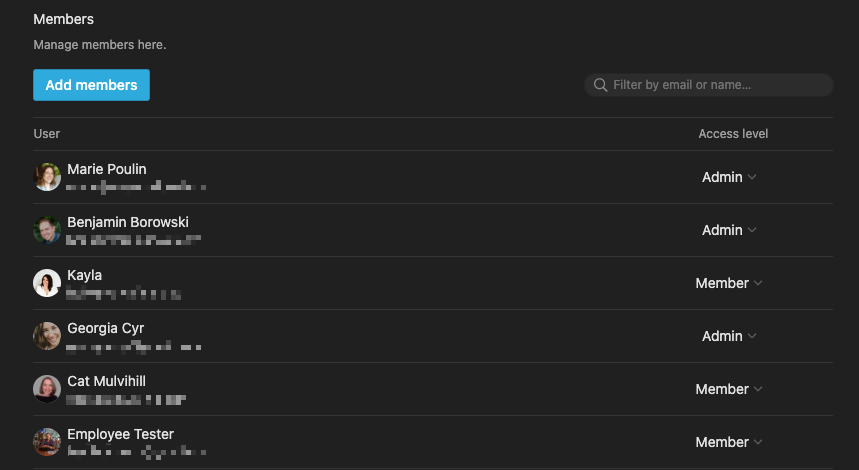
This works for both Members and Guests, so you should be incredibly careful of who you invite into your Workspaces, even on a single page.
This makes collaborating with external clients or others a bit tricky at times, and sometimes even a non-starter. For example, if you were an agency working with multiple clients, some of those clients might be in competition with each other. Knowing that they were both working with you might be considered a trade secret, and something you may want to keep private from each client.
Important takeaway: You may have to update your privacy policies and code of conducts to accommodate this unfortunate product feature.
Good Practices
Given the current security and privacy implications, in general (and with Notion), I recommend the following practices to keep your email and Notion accounts as secure as possible.
- Password manager is non-optional.
- Never share passwords in plain text: not in email, not in Slack, nothing. NO!
- Use multi-factor authentication whenever possible, especially on email, financials, domain management, et al (even if it’s annoying).
- Use multi-factor authentication with secondary hardware if accessible; avoid SMS MFA if possible (reduces SIM-jacking potential).
- Audit apps that have access to primary tooling (example: sharing Google Calendar/Mail access).
- Make it difficult or impossible for employees to make changes to authentication/apps without permission.
- Update your privacy policies and terms to include language about email exposure inherent with Notion’s current feature set.
[*For full disclosure, I’m a Notion Partner, so when you sign up with my link, you also help support me and my content!]

 Notion tips in your inbox
Notion tips in your inbox